What would happen if you had a multi-location hospitality business and had to close multiple locations? If a possible data breach and ransomware attack occurred, holding files hostage and eroding the trust of your customer base? What next?
“It is already common and will become more and more so,” said CEO Ryan Vestby. “The idea that the core technology in your business, the everyday tools that you use, can and will be used against you. If not properly protected, they become penetration points, leaving holes in your system for malicious intent. You wouldn’t leave your purse or wallet on the seat of your car after you have parked your vehicle and walked away with the doors unlocked. The same rules apply to technology today. It needs to be monitored with up-to-date hardware and software that is forever changing. Therefore the work to secure systems properly is never complete. We have an entire society to educate on how important becoming technology-centric is to a business. Ultimately it affects the bottom line. Bad technology drives inefficiencies to a business’s payroll with a multi-pronged approach, yet technology is a line item that most businesses don’t budget enough for.”
Recipe Unlimited has franchises and/or operates over 1,000 restaurants on a national level, mainly in Canada.
Sophia Harris, Business Reporter for the CBC, has been on top of this story and shares employee confusion, concern, and what she calls a “downplaying” of the ransomware letter received by Recipe Unlimited.
Without knowing the full scale of the attack it is hard to pinpoint exactly what type it could be. All signs currently point to a targeted ransomware campaign called Ryuk.
What is Ryuk?
Ryuk is a targeted and very well-planned ransomware campaign. It has attacked organizations worldwide, with payouts ranging from 15-50 BTC (Bitcoin). While common ransomware uses a systematically distributed email with a mass spam campaign, targeting employees by encouraging them to click links or open attachments, Ryuk is tailored. Its scheme is intentional and built for smaller-scale operations. It infects crucial resources like a POS (Point Of Sale) system and is carried out manually by the attacker. This means it has had to extensively research, map, hack, and collect data prior to you knowing you have been attacked. The attackers are experienced and target the vulnerabilities of your operation.
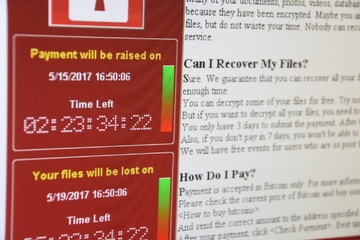
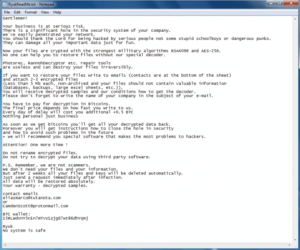
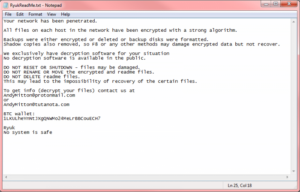
Then, they leave you a note.
Ryuk’s Ransom Note Examples
To read more about Ryuk from a technical standpoint there is an in-depth blog by Checkpoint Research.
Malware VS Ransomware
Malware disrupts and damages your system by gaining unauthorized access. Simply put, it is short for malicious software. It is designed to intentionally infect your system and comes in the form of a computer virus or worm, Trojans, spyware, adware, and ransomware.
Ransomware, on the other hand, is a subset of malware that is designed to block access. It is most common to penetrate connected devices or systems, such as a personal computer, server, pos-system, smartphone, or tablet. A ransom is paid to unlock and hopefully regain access, but there is no guarantee.
Penetration Testing – Ethical Hacking
Core security is as important as keeping the lights on for a business today. A penetration test or pen test is an evaluation of the security layers of your technology infrastructure. It is concerned with safely trying to exploit vulnerabilities.
Vulnerabilities may exist in operating systems, services, application flaws, improper configurations, or risky end-user behaviour. Such assessments are also useful in validating the efficacy of defence mechanisms, as well as end-user adherence to security policies.
Once you know where the penetration risks are, you can start to plan and manage prevention strategies in an intelligent way. This also avoids the cost of network downtime and preserves the corporate image and customer loyalty.
Questions to ask your current provider
- The easiest place to breach security is not always your technology but your employees. Has training been conducted to educate staff on what to watch for? Does your provider offer this training?
- Do you conduct scheduled testing of both internal and external systems using known attacker tools and methodologies?
- Do you have an incident response plan should a breach occur?
- Do you currently use an industry-grade firewall to protect your environment?
- Does your network have multiple layers of security for attackers to overcome? What are they?
- Is company data backed up using block-level, incremental forever technology? Does the solution allow backups as often as every 15 minutes?
- Do you offer spear phishing and social engineering simulations?
- Do you use information governance to know where your critical value data resides?
- Are you using a next-generation, AI-based security platform on workstations and servers? Or does your solution still need to complete slow scans?
- Have you established an organization-wide awareness campaign to educate all employees on common attacks?